Cyber Essentials
Cyber Essentials is a globally recognised IT security standard developed by the UK’s National Cyber Security Centre, which is used to ensure that IT software and processes are secure and organisations are protected from data breaches and leaks. It may be a mandatory certification required by governments and large organisations when working with suppliers on sensitive projects.
Cyber Security Certifications
Cyber attacks are a real threat to an organisation, and unauthorised access to sensitive data through supply chain and technical controls is becoming more common due to increasing cyber threats at different levels of the cyber. With most information and data now based online on connected servers and cloud-based services, having secure IT software and processes is crucial to prevent cybercrime and data breaches of sensitive information.
Gaining Cyber Essentials certification allows organizations to showcase trustworthy security credentials and demonstrate their commitment to cyber security by implementing technical controls to safeguard their devices and software.
- Enhance data security processes and policies to protect data from cyber threats.
- Achieve Cybersecurity certifications with an internationally accredited certification body to reduce the risk of unauthorised access.
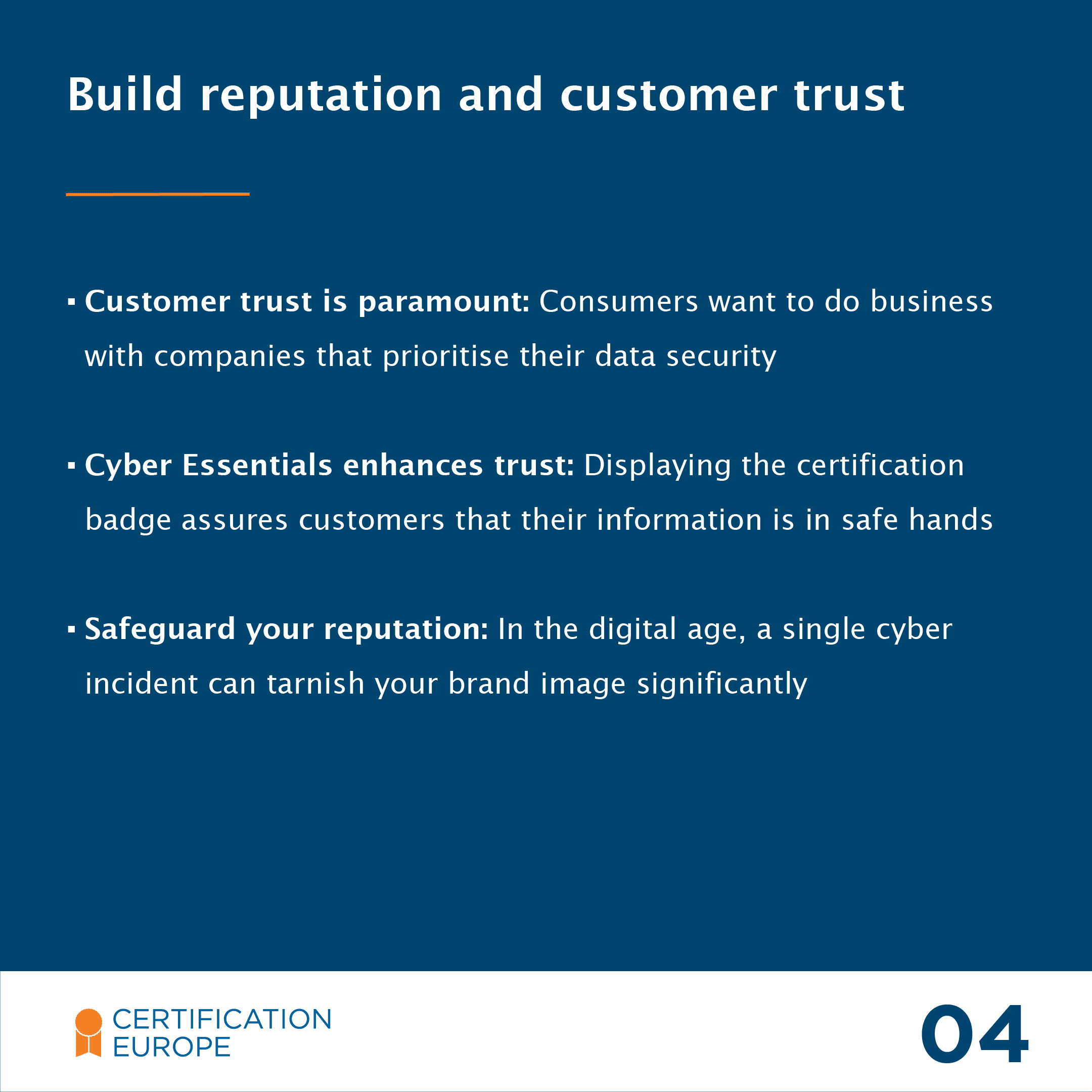
- Demonstrate robust IT and data security systems to build customer trust and protect sensitive data.
- Reduce the risk of reputational harm through data breaches and cyber-attacks by ensuring secure supply chain.
- Protect organisational assets, IP, sensitive and commercial data with advanced technical controls.
Certifications

Cyber Essentials Certification

Cyber Essentials Plus Certification
Cyber Essentials Plus Certification is a technical audit of your system.
A qualified assessor examines the same five controls, testing that they work through a technical audit.
What are the benefits of Cyber Essentials certification?
Cybersecurity certifications ensure that your organisation’s IT is protected, with measures to reduce security risks and put in place a plan of action in the event of a cyber attack.
Some of the benefits of implementing Cyber Essentials control include:
- Improves your organisation’s information security at a time where data protection has never been more critical.
- Helps ensure compliance with General Data Protection Regulations (GDPR) across the European Union and the UK.
- Reduces the risk of hefty fines from data breaches or not adhering to data protection legislation.
- Helps win contracts and new business with UK organisations, where Cyber Essentials is required.
- Demonstrates a level of commitment towards protecting the data you process.
- Boosts your reputation and increases trust among your clients, stakeholders and employees.
How do I become certified?
Certification Europe operates our Cyber Essentials service offering via our sister company, Ascentor.
Ascentor, an Amtivo Group Company (just like Certification Europe) is made up of leading Cyber Security Specialists who bring unrivalled experience to their client base in the field of cyber risk management. Ascentor work alongside Certification Europe to bring our clients a seamless certification experience.
To begin your journey toward achieving Cyber Essentials, Cyber Essentials Plus or IASME Cyber Assured, please complete the enquiry form at the bottom of this page and one of the dedicated sales coordinators at Ascentor will contact you to discuss your requirements further.

Cyber Essentials Certification Process
This is the basic level of certification for Cyber Essentials. Certification Europe operates this certification through our sister company, Ascentor, who will support you through the certification process. Certification is achieved by a verified, self-assessed online questionnaire, covering information on your firewalls, malware protection, patch management, secure configuration of your devices and access control.
Process
- Purchase Cyber Essentials Basic Certification by contacting the Ascentor Team using the form below.
- The team will be in touch to provide you with your credentials to access your questionnaire.
- You fill in the online questionnaire. Ascentor’s assessor will then review your answers and advise of any required changes before submission for certification.
- You submit your online questionnaire for certification once you and the assessor are happy.
- If successful, you will receive your certificate.

Cyber Essentials Plus Certification Process
Do you already have Cyber Essentials and would like to secure Cyber Essentials Plus certification?
Cyber Essentials Plus requires a remote technical assessment of your system which includes a review of how you are meeting the 5 categories of Cyber Essentials.
Process
- Contact the Ascentor Team using the form below.
- The team will confirm that your current Cyber Essentials Basic Certificate has been issued within the last 3 months.
- The team will assess the number of days testing and assessment will require and issue a quotation.
- The team will arrange a convenient time for the remote assessment to take place.
- If all criteria are met during the assessment, you will receive your Cyber Essentials Plus Certificate and report.
* If you need support in addressing any issues identified throughout the certification process, please contact us.
Frequently Asked Questions
Cyber Essential is suitable for any organisation that requires a base-level security certification to demonstrate it has vital controls in place.
Cyber Essentials is also mandatory for businesses seeking UK government-specific contracts; without the certification, your organisation won’t be able to bid for such contracts.
A Cyber Essentials certificate is 12 months certification and should be renewed annually due to the ever changing cyber world.
Boundary Firewalls and Internet Gateways
Your first line of defence against an intrusion from the internet will be boundary firewalls and internet gateways. A well-configured firewall can prevent breaches before they penetrate deep into your network. At the same time, an internet gateway can deny users within your organisation to websites or other online services that present a threat.
Secure Configuration
Some setup and configuration will be required to ensure your hardware and software provide the most effective protection. Removing unused software and services from your devices will reduce the number of potential vulnerabilities as older versions of some widespread software have well-documented security vulnerabilities. It is also to ensure that you remove any default passwords used by software and hardware as these are well-known by hackers.
Access Control
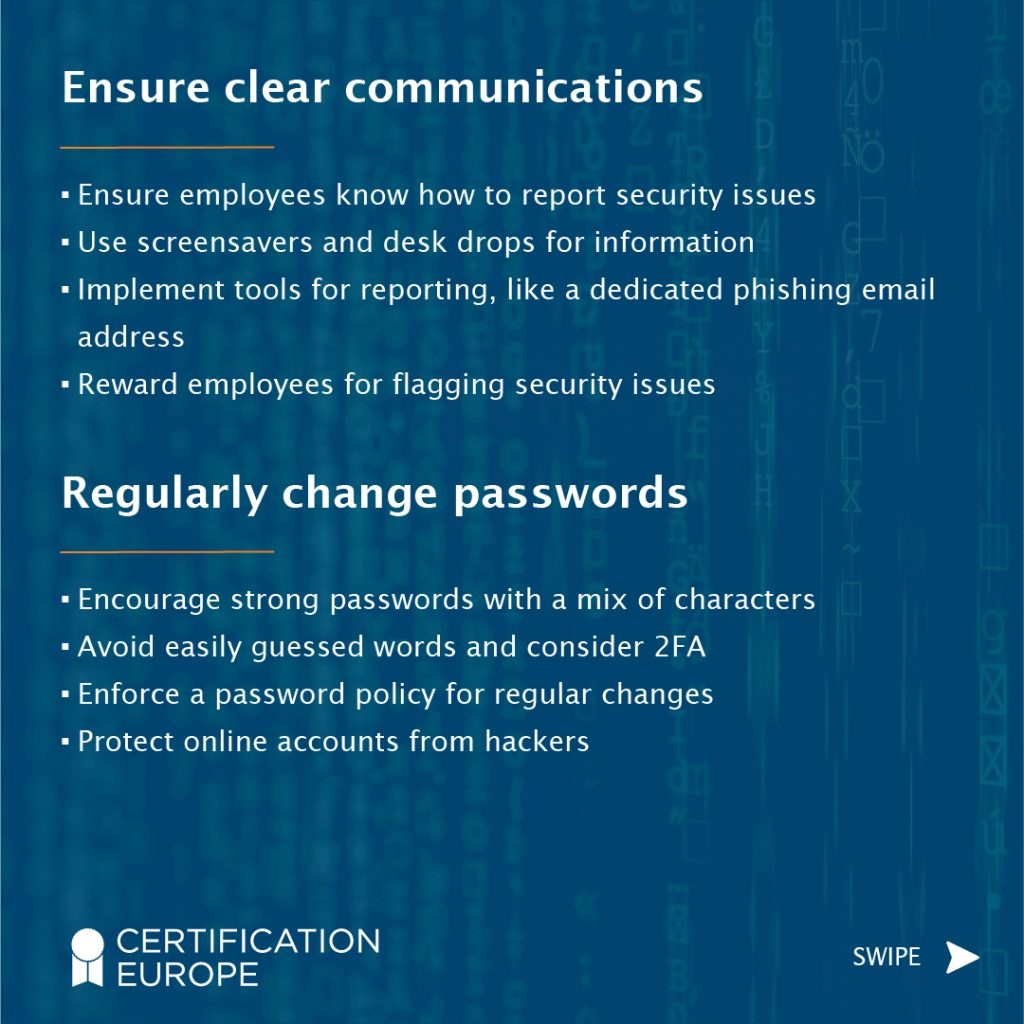
Access to your system should be restricted to trusted users, so each of these users must have and use their username and password, which is appropriate to the job they are undertaking at the time. Administrator accounts should only be used when strictly necessary, such as installing known and trusted software.
A brute force password attack is a common method of attack, perhaps even by casual users trying to access your Wi-Fi. Therefore, you need to enforce strong passwords and frequent password changes and limit the number of failed login attempts. Passwords or other access should be cancelled immediately should a staff member leave the company or is absent for long periods.
Malware Protection
Malware is malicious software specifically designed to disrupt or damage a computer system. You should have anti-virus or anti-malware products regularly scanning your network to prevent or detect threats. You will also need to keep them up-to-date and switched on to continually monitor your computer system.
You should also make sure you receive and act upon any alerts issued by the malware protection.
Patch Management and Software Updates
Computer equipment and software need to be maintained regularly to fix any security vulnerabilities and keep it running smoothly. Security software such as anti-virus and anti-malware need regular updates to provide adequate protection. Checking regularly for updates and subsequently applying them will keep your software up-to-date, and most software can also be set to update automatically.
If your system is a few years old, you should review the protection you have to ensure it is still adequate. In between updates, you should use patches to maintain your computer system. A patch is a software designed to update a computer program or its supporting data to fix or improve it. This includes fixing security vulnerabilities and other bugs, with such patches usually called bug fixes, and improving usability or performance.
Would you like a quote for ISO Certification Services?
Our team are here to help! Click the button below to complete our enquiry form for “Certification Services” and our team will be in touch with a quote and further information!
Our latest LinkedIn insights