ISO 27001
Information Security Management Systems
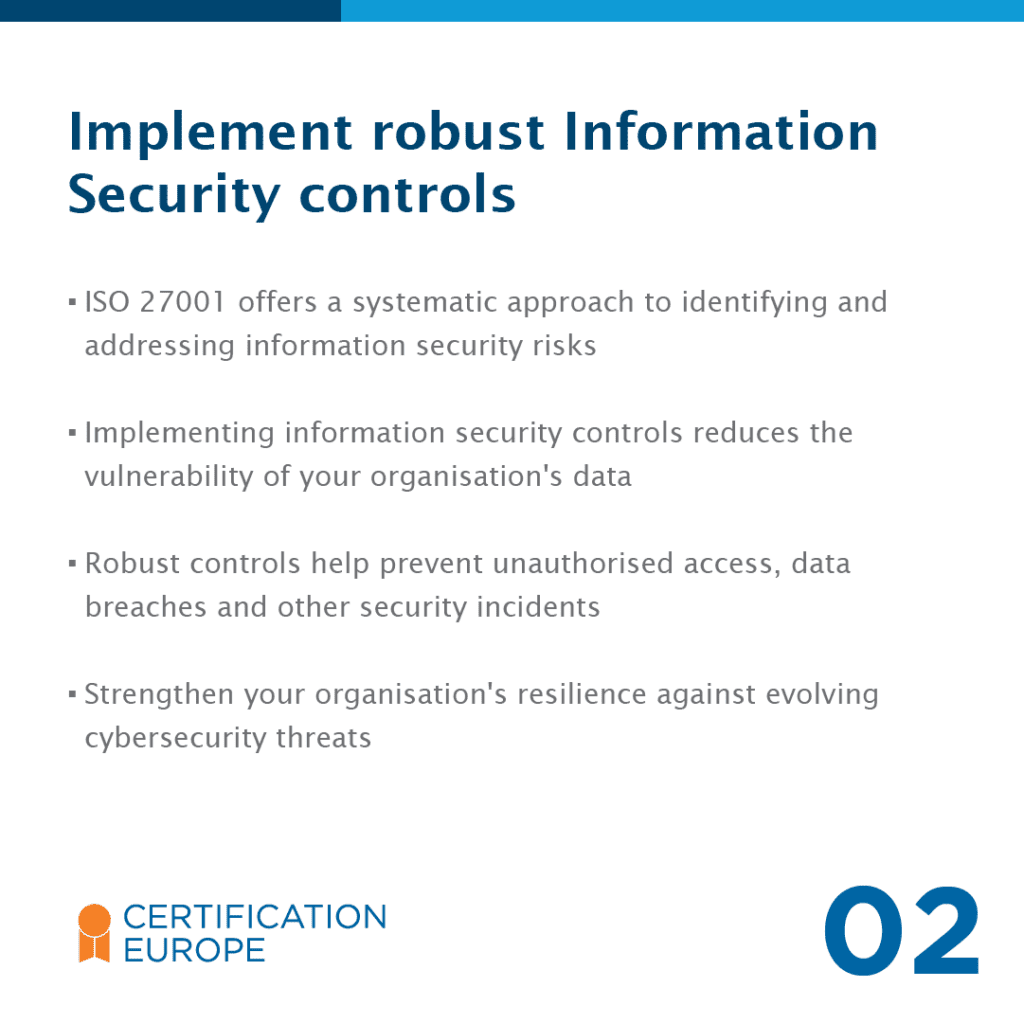
ISO 27001, also known as ISO/IEC 27001, is the internationally recognised global standard for managing risks related to the security of information and data your organisation holds. This standard ensures that customer and employee data is stored securely and complies with legal requirements such as GDPR. It adopts a process-based approach for establishing, implementing, operating, monitoring, maintaining, and improving your Information Security Management System (ISMS).
What is ISO 27001?
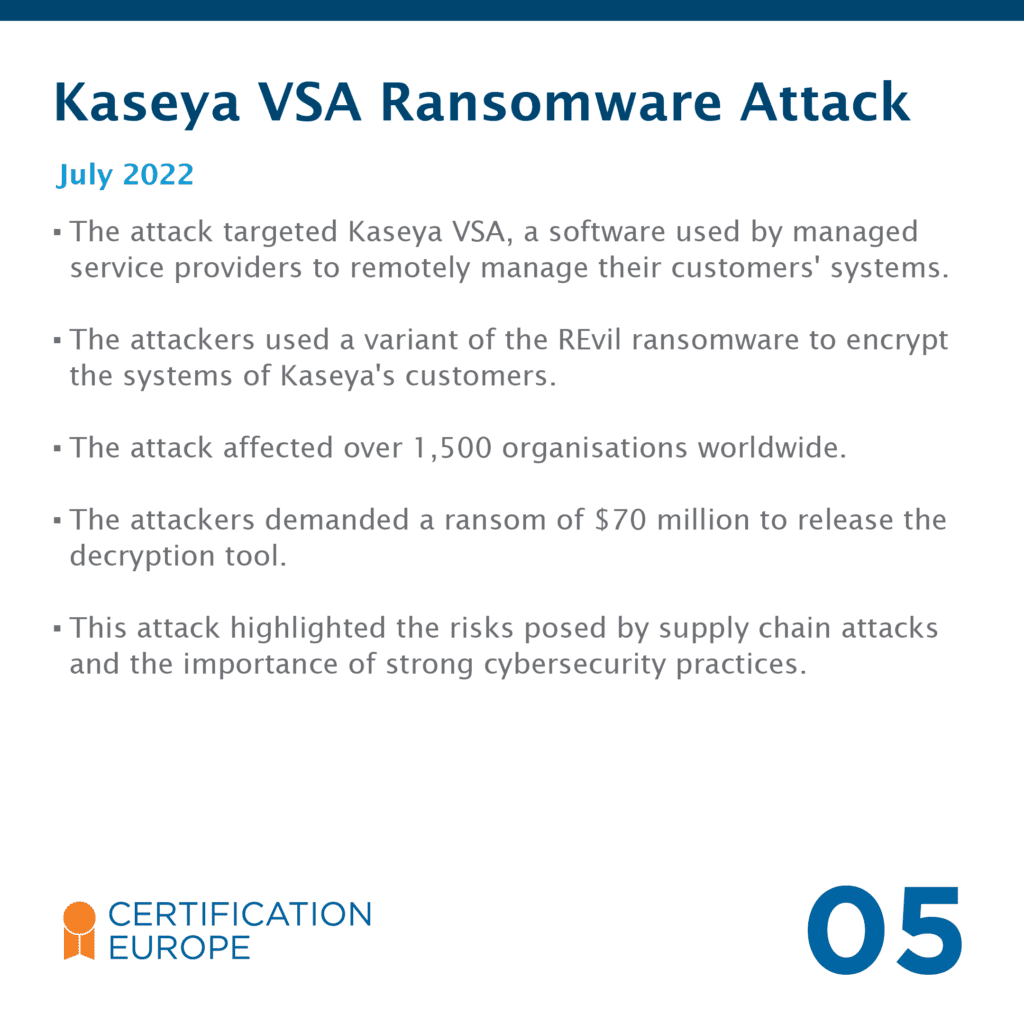
A key priority for organisations is to secure the data and information they hold. With high-profile data breaches and cyber security attacks such as ransomware, customers require organisations to handle, secure and store data and information to the highest standard.
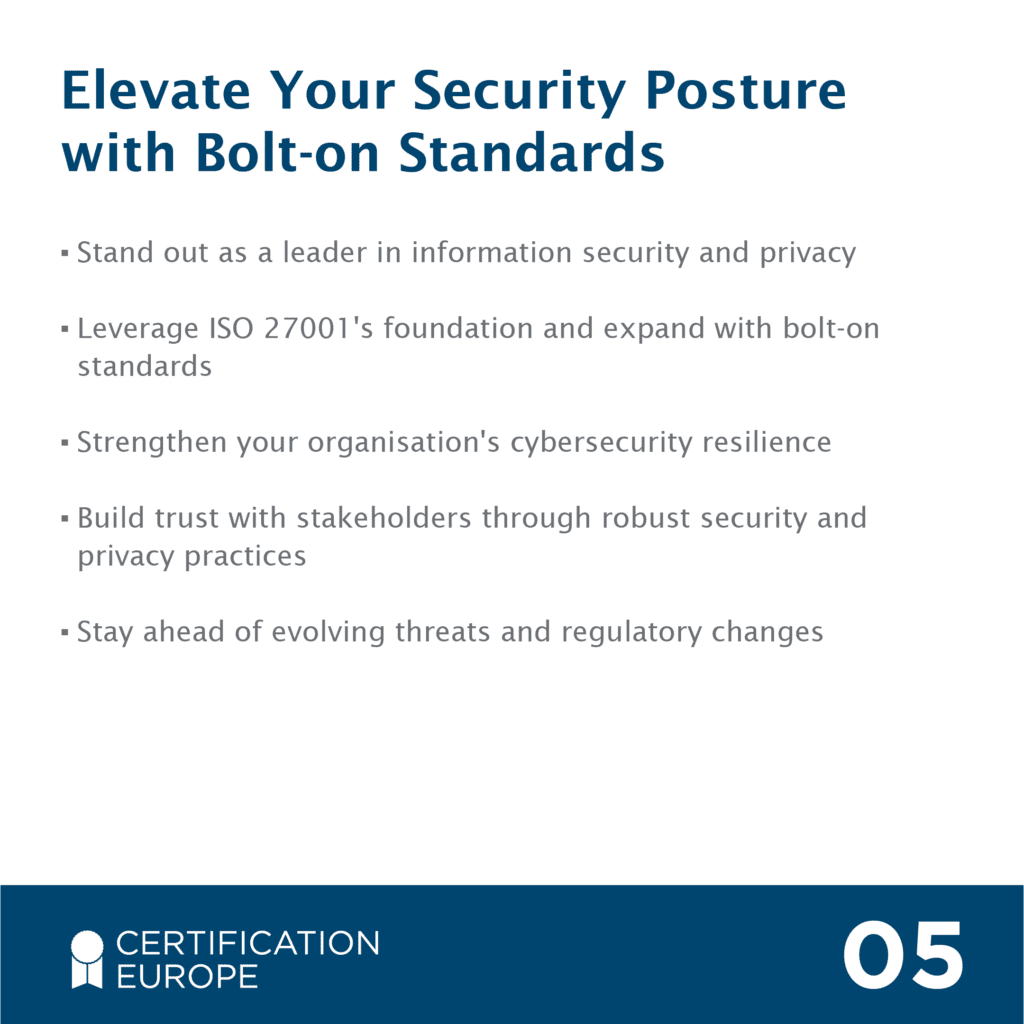
ISO 27001, also known as ISO/IEC 27001, is the world’s best-known standard for Information Security Management Systems (ISMS). It provides a systematic and comprehensive approach to managing and protecting sensitive information within an organisation. Certification to ISO 27001 is valuable to organisations looking to enhance their cybersecurity posture and demonstrate their commitment to protecting sensitive information.
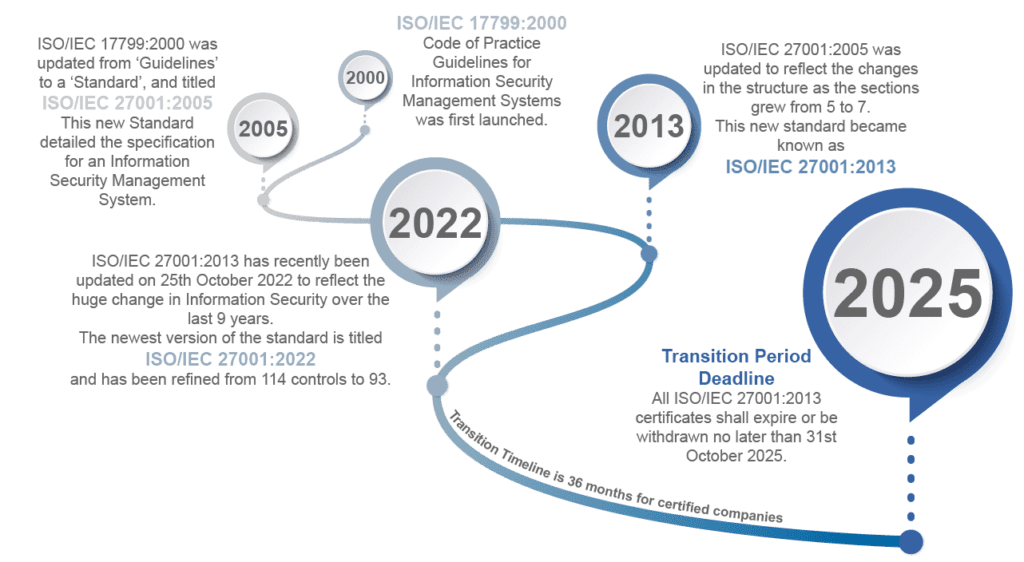
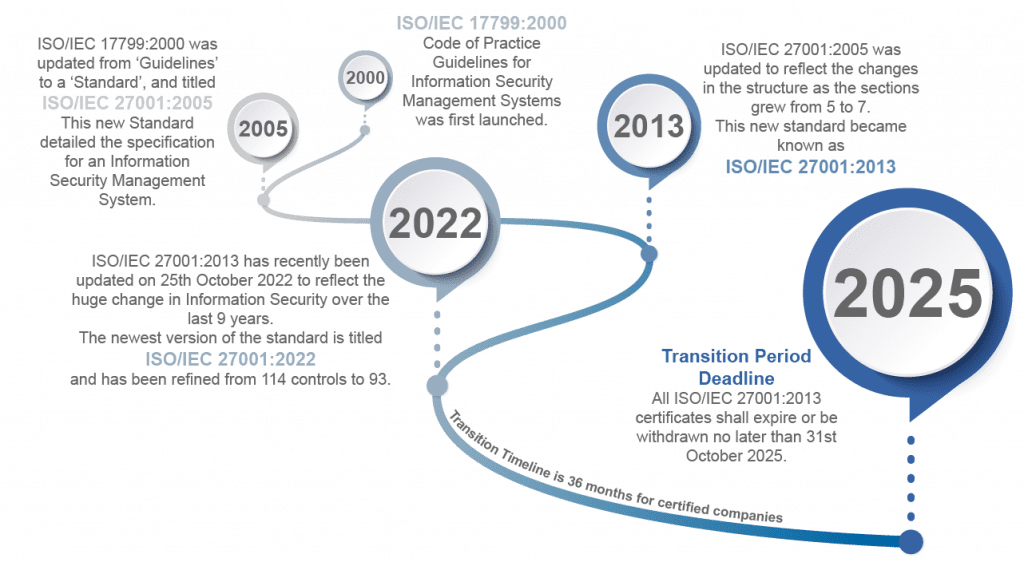
The standard was developed by the International Organization for Standardization and is part of the wider ISO/IEC 27000 family. It was recently updated from the 2013 version of the standard to the 2022 version and the latest version of the standard is known as ISO/IEC27001:2022.

What are the benefits?

Confidentiality Assurance

Secure Data Exchange

Regulatory Compliance

Data Protection
Competitive Advantage
Enhanced Trust
Consistent Delivery

Risk Reduction

Cultural Security

Organisational Protection
Strong Internal Processes

Continuous Improvement
Key Requirements of ISO 27001
The ISO 27001 standard outlines a number of requirements that organisations must meet to demonstrate their commitment to information security. These include
Risk Assessment: Identify and assess the risks to your organisation’s information assets. This includes understanding the potential threats, vulnerabilities and impacts.
Security Policies: Develop comprehensive information security policies and procedures that cover all aspects of your ISMS. These policies should be aligned with the organisation’s objectives and risk assessment findings.
Information Security Roles: Define the roles and responsibilities related to information security within your organisation. Assign roles such as Information Security Manager and Data Protection Officer, as needed.
Asset Management: Maintain an inventory of information assets and classify them based on their importance and sensitivity. Implement controls to protect these assets accordingly.
Access Control: Ensure that access to information and systems is restricted to authorised personnel only. Implement user access controls, including user authentication and authorisation.
Security Awareness: Train and raise awareness among employees about information security. Ensure that your staff understands their roles in maintaining security.
Incident Response: Develop an incident response plan to handle security incidents effectively. This should include steps for reporting, assessing, and mitigating security breaches.
Monitoring and Measurement: Continuously monitor the performance of your ISMS and gather data to measure its effectiveness. Use this information to make improvements where necessary.
Business Continuity: Develop a business continuity plan to ensure that critical processes and information can be maintained in the event of disruptions or disasters.
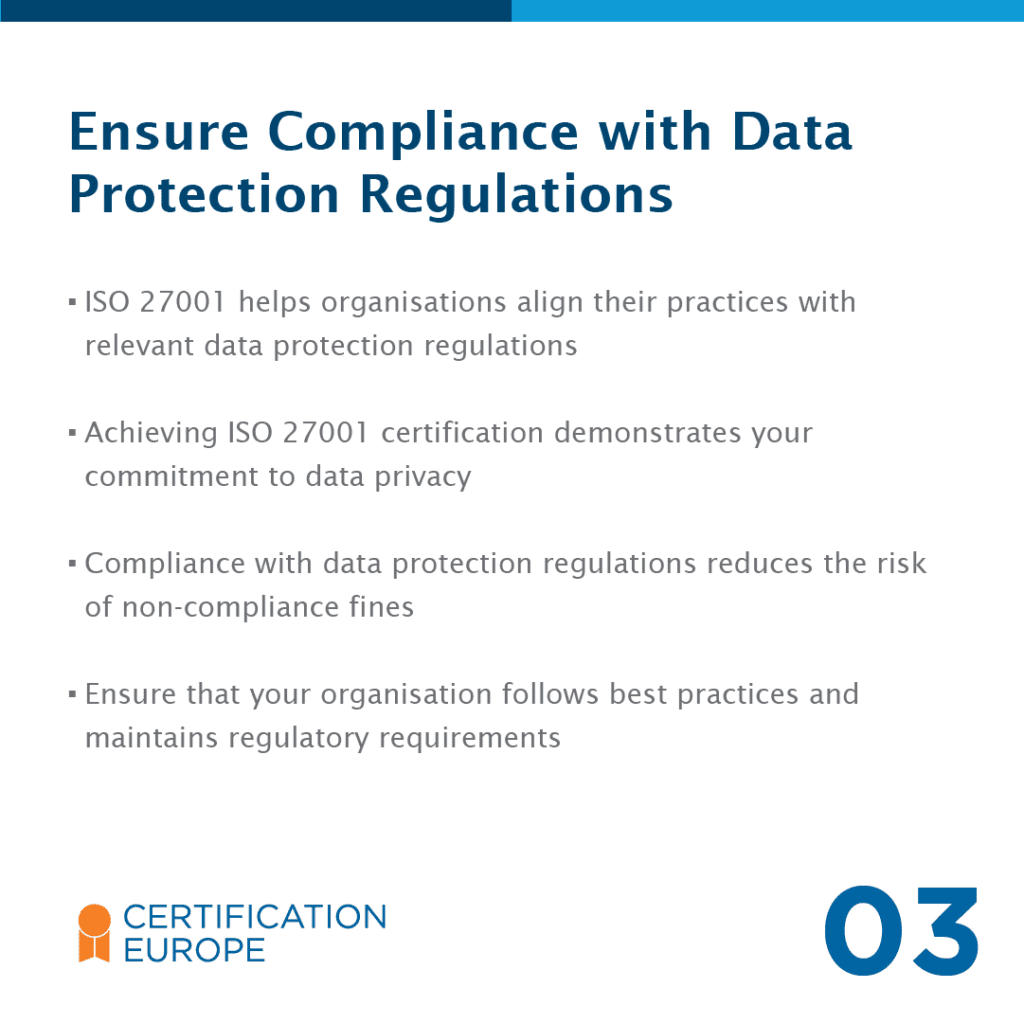
Compliance: Ensure that your ISMS aligns with relevant legal and regulatory requirements, such as GDPR, and maintain documentation to demonstrate compliance.
FAQs on the updated ISO/IEC 27001 Standard
Since this standard was last updated back in 2013, the information security industry has transformed significantly through the types of new technologies available to us all, such as the cloud.
The level of intellectual property and information assets we hold come with new and emerging threats and risks. This has resulted in the requirement for ISO 27001 to be updated to ensure it stays effective and relevant.
The overall structure of ISO/IEC 27001’s Annex SL clauses have not changed. These clauses include:
- Clause 4 – Context of the organization
- Clause 5 – Leadership
- Clause 6 – Planning
- Clause 7 – Support
- Clause 8 – Operation
- Clause 9 – Performance evaluation
- Clause 10 – Improvement
The clauses have, however, undergone minor changes including wording, structuring of sentences and some additional new content.
Annex A has had the most significant changes, with the number of controls being refined from 114 in ISO 27001:2013 to 93 in ISO/IEC 27001:2022. These controls have been restructured and merged to align into 4 control sections, instead of the previous 14 sections.
When an organisation is certified to ISO 27001, it means they have controls in place to identify, manage and mitigate risks and have secure systems in place. With cyber-attacks more common than ever, this updated version of the standard offers confidence, assurance and certainty to businesses that their information security management system stays on top of the risks. It also demonstrates to your customers that you take information security seriously and are prepared for any attacks on your system(s).
If your business is currently certified to ISO 27001:2013, you will need to transition to the new standard before the Transition Period Deadline.
There is a transition period of 36 months for certified companies. This runs from 25th October 2022 to 31st October 2025, giving certified companies plenty of time to comply.
Our ISO/IEC 27001:2022 Transition Policy, available for download below, contains useful information to help you through the Transition Period.
We have also created two helpful timeline images available to view below:
- Key Dates for Existing ISO 27001:2013 Certification Clients
- Key Dates or New ISO 27001:2013 Certification Clients
Certification Europe offers a Transition Training Course available to anyone who wants to learn more about the differences between ISO 27001:2013 and ISO/IEC 27001:2022.
Alternatively, feel free to get in touch with our team if you have any questions.
FAQs on the updated ISO/IEC 27001 Standard
Since this standard was last updated back in 2013, the information security industry has transformed significantly through the types of new technologies available to us all, such as the cloud.
The level of intellectual property and information assets we hold come with new and emerging threats and risks. This has resulted in the requirement for ISO 27001 to be updated to ensure it stays effective and relevant.
The overall structure of ISO/IEC 27001’s Annex SL clauses have not changed. These clauses include:
- Clause 4 – Context of the organization
- Clause 5 – Leadership
- Clause 6 – Planning
- Clause 7 – Support
- Clause 8 – Operation
- Clause 9 – Performance evaluation
- Clause 10 – Improvement
The clauses have, however, undergone minor changes including wording, structuring of sentences and some additional new content.
Annex A has had the most significant changes, with the number of controls being refined from 114 in ISO 27001:2013 to 93 in ISO/IEC 27001:2022. These controls have been restructured and merged to align into 4 control sections, instead of the previous 14 sections.
When an organisation is certified to ISO 27001, it means they have controls in place to identify, manage and mitigate risks and have secure systems in place. With cyber-attacks more common than ever, this updated version of the standard offers confidence, assurance and certainty to businesses that their information security management system stays on top of the risks. It also demonstrates to your customers that you take information security seriously and are prepared for any attacks on your system(s).
If your business is currently certified to ISO 27001:2013, you will need to transition to the new standard before the Transition Period Deadline.
There is a transition period of 36 months for certified companies. This runs from 25th October 2022 to 31st October 2025, giving certified companies plenty of time to comply.
Our ISO/IEC 27001:2022 Transition Policy, available for download below, contains useful information to help you through the Transition Period.
We have also created two helpful timeline images available to view below:
- Key Dates for Existing ISO 27001:2013 Certification Clients
- Key Dates or New ISO 27001:2013 Certification Clients
Certification Europe offers a Transition Training Course available to anyone who wants to learn more about the differences between ISO 27001:2013 and ISO/IEC 27001:2022.
Alternatively, feel free to get in touch with our team if you have any questions.



Implementing ISO 27001:2022
Ensuring your IMS is ready for ISO 27001:2022 certification involves commitment from the whole organisation. You may wish to have a Certification Body conduct a Gap Analysis to review the readiness of your IMS before going through the Certification Assessments.
As well as a Gap Analysis, Training Courses are also a good way to ensure your teams are prepared and understanding of what ISO 27001:2022 certification involves. Certification Europe provides ISO 27001 Introduction, Lead Auditor, Advanced Risk & Implementation, Risk Management and ISMS Champion training opportunities to support you. These courses, led by experts in the field of Information Security Management cater to diverse organisational requirements, encompassing implementation strategies, internal auditing techniques and continuous improvement practices.
To find out more, click the course titles on the right or get in touch with our Training Team.
Ensuring your IMS is ready for ISO 27001:2022 certification involves commitment from the whole organisation. You may wish to have a Certification Body conduct a Gap Analysis to review the readiness of your IMS before going through the Certification Assessments.
As well as a Gap Analysis, Training Courses are also a good way to ensure your teams are prepared and understanding of what ISO 27001:2022 certification involves. Certification Europe provides ISO 27001 Introduction, Lead Auditor, Advanced Risk & Implementation, Risk Management and ISMS Champion training opportunities to support you. These courses, led by experts in the field of Information Security Management cater to diverse organisational requirements, encompassing implementation strategies, internal auditing techniques and continuous improvement practices.
To find out more, click the course titles on the right or get in touch with our Training Team.
Useful Resources

Download ISO/IEC 27001:2022 Transition Policy
Certification Europe is thrilled to be one of the first organisations in Europe to be accredited to ISO/IEC 27001:2022!


ISO 27001 Transition Webinar Recording
Unlock the Webinar Video Now! Access the recording of our ISO 27001:2022 Transition Webinar with Dr. Luke Feeney, Information Security Expert.

ISO 27001 - Pogust Goodhead Case Study
Explore how Pogust Goodhead achieved ISO 27001 certification with Certification Europe, enhancing data security & client trust.
Becoming Certified to ISO 27001
Stage One
The initial assessment determines if the mandatory requirements of the standard are being met and if the management system is capable of proceeding to Stage 2.
Stage Two
The second assessment determines the effectiveness of the system, and seeks to confirm that the management system is implemented and operational.
Recommendation for Certification
At this point in the process we review any corrective actions taken to address findings raised at Stage 1 & 2. Certification may be recommended.
Certification Review & Decision
The organisations files are reviewed by an independent and impartial panel and the certification decision is made.
Certification Achived
Successful certification is communicated to the client. Certificates are issued.



Becoming Certified to ISO 27001
Stage
One
The initial assessment determines if the mandatory requirements of the standard are being met and if the management system is capable of proceeding to Stage 2. Recommendation for Certification
At this point in the process we review any corrective actions taken to address findings raised at Stage 1 & 2. Certification may be recommended.

Certification
Achieved
Successful certification is communicated to the client. Certificates are issued. Stage
Two
The second assessment determines the effectiveness of the system, and seeks to confirm that the management system is implemented and operational. Certification Review & Decision
The organisations files are reviewed by an independent and impartial panel and the certification decision is made.ISO 27001 FAQs
Certification Europe is accredited by INAB to ensure that the services we provide are exceptional and meet rigorous international certification standards.
Accreditation is the process by which a certification body is recognised to offer certification services. To become accredited, Certification Europe is required to implement a Quality Management System which is accredited by INAB (Irish National Accreditation Body).
We’re audited annually to ensure our services meet the exact requirements of the relevant accreditation standards.
Our expertise is proven, and you can read about them on our website. We launched the first accredited scheme for ISO 27001 in Ireland and the first accredited scheme for BS 7799.
ISO 27001:2022 is the latest version of the ISO 27001 standard and part of the wider ISO 27001 family. We use the most up-to-date ISO standard to meet mandatory certification requirements.
ISO 27001 certification is suitable for any organisation, large or small, in any sector. The standard is especially relevant where information protection is critical, such as banking, financial, health, public, and IT. The standard is also applicable to organisations that manage high volumes of data or information on behalf of other organisations such as data centres and IT outsourcing companies.
The information security management standard lasts for three years and is subject to mandatory audits to ensure compliance. At the end of the three years, you will need to complete a reassessment audit to receive the standard for an additional three years.
Certification Europe offers ISO 27001 Implementation and Lead Auditor dedicated ISO training courses.
Would you like a quote for ISO 27001 Certification Services?
Our team are here to help! Click the button below to complete our enquiry form for “ISO 27001 Certification Services” and our team will be in touch with a quote and further information!
Related ISO Certifications


Quality Management System
ISO 9001 is an internationally recognised global standard that confirms an organisation’s commitment to improving quality, delivering more efficient operations and improving customer satisfaction....


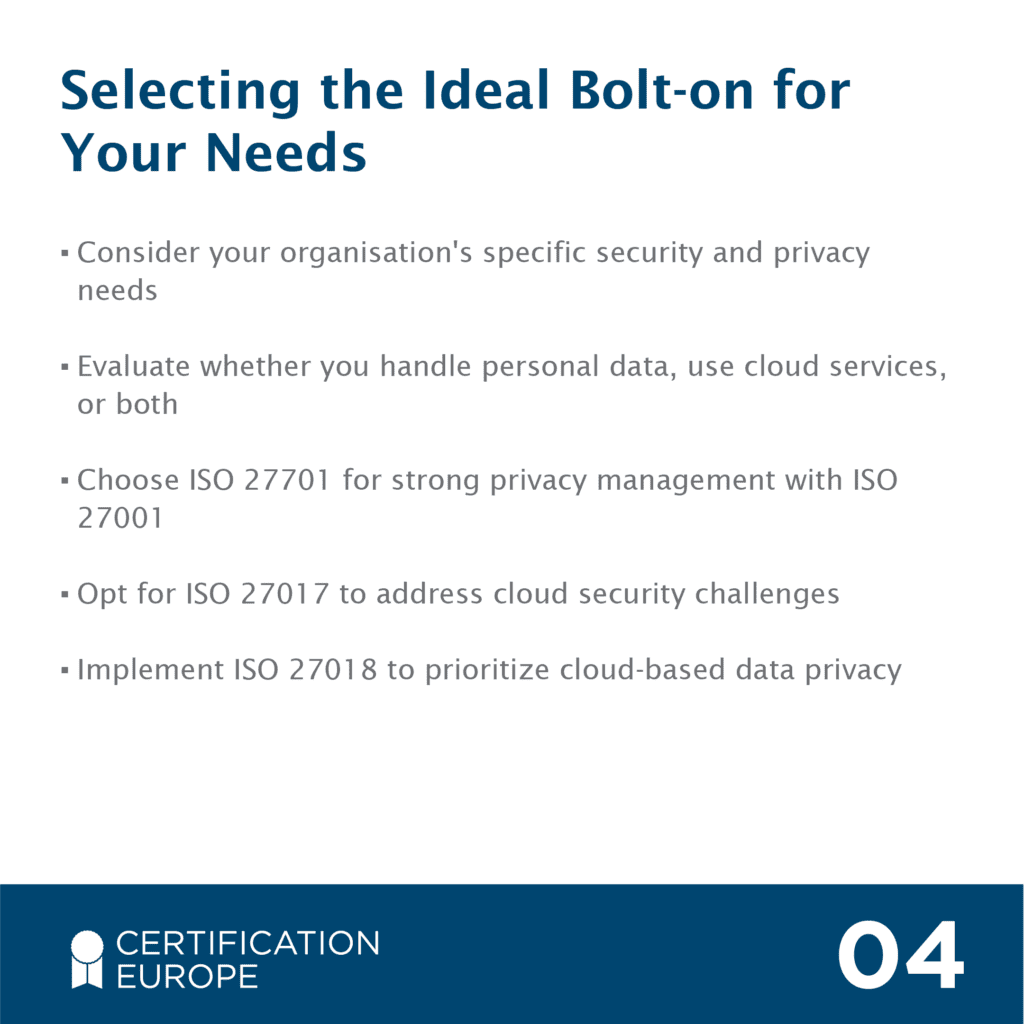
Privacy Information Management Systems
ISO 27701 is the global standard for Privacy Information Management Systems (PIMS), also known as the PIM system. Developed by ISO, it helps organisations better...


Cloud Data Protection
ISO 27017 is the global standard used by organisations to strengthen their current cloud data protection and cloud security services. The standard highlights the actions..


Protection of Personally Identifiable Information (PII)
ISO 27018 is the global standard organisations use to implement and manage systems that protect Personally Identifiable Information (PII), such as sensitive customer...


Business Continuity Management Systems
ISO 22301 provides a framework that helps protect companies from the risks associated with downtime, which can occur due to unexpected impact of disruptions or ...


IT Service Management Systems
ISO 20000-1 Service Management is the international standard for quality management specifically focused on IT service management. It ensures the design, operation, control, and delivery of an...
Our latest LinkedIn insights



























































































































Related Insights


How to save energy with a carbon footprint calculator
Irish businesses believe that Big Data, analytics and cloud technologies will deliver the most value over the next two years. EY’s Tech Horizon Report, which explores how technology and transformation can...


How to handle a subject access request (SAR)
Under GDPR guidance, individuals are entitled to access their personal data stored by an organisation. These requests are known as Subject Access Requests (SAR) or Data Subject Access Requests (DSAR).


ISO 27001 guide for beginners
Over 35,000 organisations across the globe are ISO 27001 certified, ensuring their information security management systems (ISMS) provide robust, compliance data protection for their business and their customers.
FAQs on the updated ISO/IEC 27001 Standard
Since this standard was last updated back in 2013, the information security industry has transformed significantly through the types of new technologies available to us all, such as the cloud.
The level of intellectual property and information assets we hold come with new and emerging threats and risks. This has resulted in the requirement for ISO 27001 to be updated to ensure it stays effective and relevant.
The overall structure of ISO/IEC 27001’s Annex SL clauses have not changed. These clauses include:
- Clause 4 – Context of the organization
- Clause 5 – Leadership
- Clause 6 – Planning
- Clause 7 – Support
- Clause 8 – Operation
- Clause 9 – Performance evaluation
- Clause 10 – Improvement
The clauses have, however, undergone minor changes including wording, structuring of sentences and some additional new content.
Annex A has had the most significant changes, with the number of controls being refined from 114 in ISO 27001:2013 to 93 in ISO/IEC 27001:2022. These controls have been restructured and merged to align into 4 control sections, instead of the previous 14 sections.
When an organisation is certified to ISO 27001, it means they have controls in place to identify, manage and mitigate risks and have secure systems in place. With cyber-attacks more common than ever, this updated version of the standard offers confidence, assurance and certainty to businesses that their information security management system stays on top of the risks. It also demonstrates to your customers that you take information security seriously and are prepared for any attacks on your system(s).
If your business is currently certified to ISO 27001:2013, you will need to transition to the new standard before the Transition Period Deadline.
There is a transition period of 36 months for certified companies. This runs from 25th October 2022 to 31st October 2025, giving certified companies plenty of time to comply.
Our ISO/IEC 27001:2022 Transition Policy, available for download below, contains useful information to help you through the Transition Period.
We have also created two helpful timeline images available to view below:
- Key Dates for Existing ISO 27001:2013 Certification Clients
- Key Dates or New ISO 27001:2013 Certification Clients
Certification Europe offers a Transition Training Course available to anyone who wants to learn more about the differences between ISO 27001:2013 and ISO/IEC 27001:2022.
Alternatively, feel free to get in touch with our team if you have any questions.

Ensuring your IMS is ready for ISO 27001:2022 certification involves commitment from the whole organisation. You may wish to have a Certification Body conduct a Gap Analysis to review the readiness of your IMS before going through the Certification Assessments.
As well as a Gap Analysis, Training Courses are also a good way to ensure your teams are prepared and understanding of what ISO 27001:2022 certification involves. Certification Europe provides ISO 27001 Introduction, Lead Auditor, Advanced Risk & Implementation, Risk Management and ISMS Champion training opportunities to support you. These courses, led by experts in the field of Information Security Management cater to diverse organisational requirements, encompassing implementation strategies, internal auditing techniques and continuous improvement practices.
To find out more, click the course titles on the right or get in touch with our Training Team.
The Certification Journey
Stage One
The initial assessment determines if the mandatory requirements of the standard are being met and if the management system is capable of proceeding to Stage 2.
Stage Two
The second assessment determines the effectiveness of the system, and seeks to confirm that the management system is implemented and operational.
Recommendation for Certification
At this point in the process we review any corrective actions taken to address findings raised at Stage 1 & 2. Certification may be recommended.
Certification Review & Decision
The organisations files are reviewed by an independent and impartial panel and the certification decision is made.
Certification Achieved
Successful certification is communicated to the client. Certificates are issued.







